Implementing a unified search platform for educational content on Amazon OpenSearch Service
AWS Public Sector Blog
NOVEMBER 15, 2024
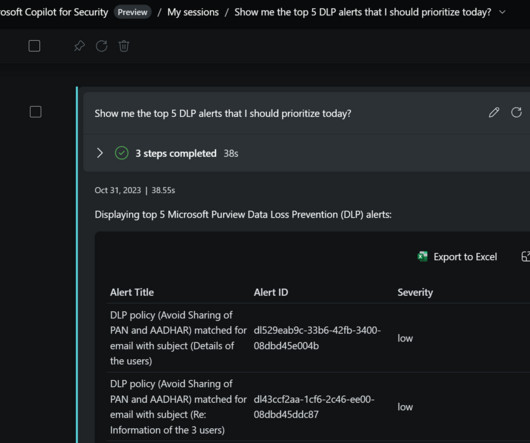
It offers industry-leading durability, availability, performance, security, and virtually unlimited scalability at very low costs, making it an ideal choice for storing large volumes of educational materials. In Query DSL, this translates to the following code.













































Let's personalize your content