Microsoft Copilot for Security and NIST 800-171: Access Control
Microsoft Public Sector
MARCH 5, 2024
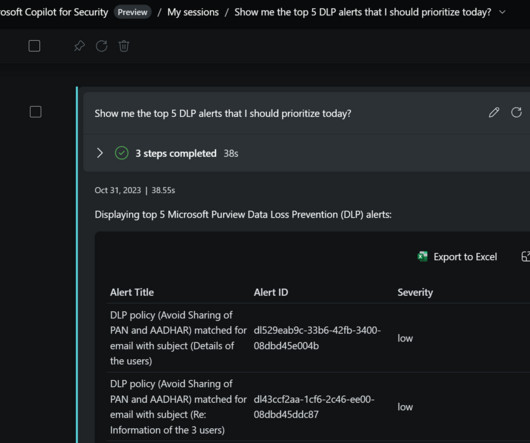
Microsoft Copilot for Security and NIST 800-171: Access Control Microsoft Copilot for Security in Microsoft’s US Gov cloud offerings (Microsoft 365 GCC/GCC High and Azure Government) is currently unavailable and does not have an ETA for availability. Future updates will be published to the public roadmap here.














































Let's personalize your content