Mass Attacks in Public Spaces, 2016-2020
Disaster Zone blog
JANUARY 25, 2023
Compiled by the Department of Homeland Security
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
 2016 Related Topics
2016 Related Topics 
Disaster Zone blog
JANUARY 25, 2023
Compiled by the Department of Homeland Security

PBB Center for Priority Based Budgeting
JULY 25, 2016
Click here for more information on the 2016 CPBB (Un)Conference. Just one week away from the highly anticipated 2016 CPBB Conference, NRC’s Angelica Wedell gets the scoop on the conference and the power of priority in this exclusive interview with the Center for Priority Based Budgeting (CPBB) Co-founder Chris Fabian.

PBB Center for Priority Based Budgeting
JUNE 28, 2016
The Center for Priority Based Budgeting 2016 "Prioritized World" (Un)Conference is just over a month away. The 2016 CPBB Unconference is going to be our biggest and most dynamic event to date! Last year NRC engaged at our 2015 conference (and is a sponsor of the 2016 conference). But don't just take our word for it.

NLC (National League of Cities)
JANUARY 25, 2023
In 2016, RUBICONSmartCity™ was launched with the goal of empowering local governments to maximize the potential and efficiency of city fleets while cutting […] Source

FedTech Magazine
JULY 5, 2023
In 2016, the National Institute of Standards and Technology asked experts to develop quantum-resistant public-key cryptographic algorithms algorithms that could be standardized for use in protecting sensitive government information. Five years later, in July 2022, the top four candidates were announced.

State Tech Magazine
SEPTEMBER 22, 2022
Through an open-data hub the city launched in 2016, residents can access charts and other resources highlighting information ranging from the number of licenses that have been issued for various types of businesses to recent attendance at the Little Rock Zoo. Web-based data analysis and visualization tools are helping Little Rock, Ark.,

FedTech Magazine
SEPTEMBER 21, 2023
Federal government cybersecurity breaches rose by 453 percent between fiscal years 2016 and 2021, according to the Government Accountability Office. To combat and overcome these threats, federal IT administrators can use IP packet capture to examine network traffic for security threats using Microsoft Network Monitor (Netmon).

Rebuilding Place in Urban Space
MARCH 6, 2024
Louis regional transit planning process as a model for what needs to be done in the DC Metropolitan region ," 2009 -- " WMATA 40th anniversary in 2016 as an opportunity for assessment ," 2014 --" What it will take to get WMATA out of crisis continued and 2016's 40th anniversary of WMATA as an opportunity to rebuild ," 2015p From March 20 to April 3, (..)

State Tech Magazine
AUGUST 17, 2022
Established in 2016 to foster job growth and economic development, the St. Petersburg Innovation District — a roughly one-square-mile area south of the city’s downtown — is now helping to spearhead the city’s smart technology efforts.

PMRA (Public Management Research Association)
JANUARY 19, 2017
One of the most frequently heard recommendations for network researchers from those who review interorganizational network papers for JPART and other top journals is “I wish you had studied this network over time.”

Rebuilding Place in Urban Space
FEBRUARY 1, 2024
. -- " Fighting blight by fixing up homes could bring down Philly gun violence, new study shows ," WHYY/NPR -- " Abandoned house repairs reduced nearby gun violenceAbandoned house repairs reduced nearby gun violence ," Penn Today (2023) -- " Urban Blight Remediation as a Cost-Beneficial Solution to Firearm Violence: A Citywide Cluster Randomized Trial (..)

GCN
AUGUST 31, 2022
If you use your mobile phone for anything other than a paperweight, your visit to the cannabis dispensary and your personality – how extroverted you are or whether you’re likely to be on the outs with family since the 2016 election – can be learned from metadata and telemetry and shared.

Eric Holdeman's Disaster Zone Podcast
OCTOBER 29, 2024
He is a frequent speaker and commentator on technology and security issues, and, since 2016, the host of the ISF Podcast featuring conversations with global industry leaders and thought leaders, including Mo Gawdat, Dr. Hannah Fry, Sir Bob Geldof, Apple founder Steve Wozniak, and the first female prime minister of Denmark, Helle Thorning-Schmidt.

GovLoop
SEPTEMBER 3, 2024
Regular inspections are an absolute necessity to prevent collapses like one that occurred in 2016. The county’s sewer transmission line serves 850,000 residents in 25 municipalities, including Detroit. That incident led to the evacuation of 23 homes and the condemnation of several houses.
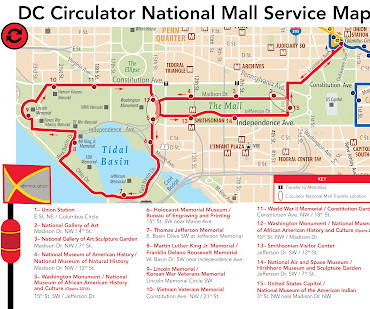
Rebuilding Place in Urban Space
MARCH 18, 2023
. -- " Should transit on Inauguration Day be free? ," 2013/2016 Note that DC will be launching free surface transit later this summer (" Free ride: DC unveils bold plan to boost public transit ," Associated Press), something I'll get around to writing about (" Is making surface transit free the best transit investment DC can make? ," 2016).

AWS Public Sector Blog
JANUARY 26, 2024
First deployed in 2016 , ICMP is a digital catalog with software listings from independent software vendors (ISVs) that makes it easy for customers in the intelligence community (IC) to find, test, buy, and deploy software that runs on AWS.

PMRA (Public Management Research Association)
JANUARY 19, 2017
Earlier this year, Dr. Marybeth Gasman of University of Pennsylvania wrote a Hechinger Report op-ed piece, where she argued that elite universities do not have diverse faculties because they do not want them.

Librarian.net
JANUARY 2, 2023
Previous years: 2021 , 2020 , 2019 , 2018 , 2017 , 2016 , 2015 , 2014 , 2013 , 2012 , 2011 , 2010 , 2009 and some reviews from 2003. Fairlee (1) – I was in town for a conference and stopped by. Hartness/Randolph (1) – Stopped by when I was in a walki I miss this place.

Citizen Lab
SEPTEMBER 20, 2022
Seattle’s Comprehensive Plan update (United States) In 2016,… The post <strong>Community engagement examples: September’s inspiring platforms</strong> appeared first on CitizenLab's Blog. We find ourselves consistently impressed by the projects launched on our platform. Let’s dive into six recent projects.

Rebuilding Place in Urban Space
FEBRUARY 27, 2024
. -- " New form of BTMFBA in San Francisco ," 2023 -- " A wrinkle on BTMFBA: let the city/county own the cultural facility, while you operate it (San Francisco and the Fillmore Heritage Center) ," 2021 -- " BTMFBA: Baltimore and the Area 405 Studio ," 2021 -- " BTMFBA: the best way to ward off artist or retail displacement is to buy the building ," (..)

Librarian.net
JANUARY 5, 2024
Previous years: 2022 , 2021 , 2020 , 2019 , 2018 , 2017 , 2016 , 2015 , 2014 , 2013 , 2012 , 2011 , 2010 , 2009 and some reviews from 2003. Hartness/Randolph (1) – I got some books out. I should go by this place more often, it’s such a nice library.

Rebuilding Place in Urban Space
MARCH 11, 2024
OTOH, there is a city regional park a few blocks away with a beautiful 2.5 acre dog park. We don't need to duplicate.)

Eric Holdeman's Disaster Zone Podcast
APRIL 25, 2023
In May 2016, Mayor James Kenney appointed Adam Thiel to serve as the 20th Fire Commissioner for the City of Philadelphia. From 2014-2016, he was a Deputy Secretary of Public Safety and Homeland Security for the Commonwealth of Virginia. How do you measure up when it comes to experience and education? and 30,000 employees.

Princeton Public Library
SEPTEMBER 13, 2021
In 2016, the municipality of Princeton joined this initiative as a Welcoming Town, and each year the Department of Human Services teams up with the library […].

Open Space Radio: Parks and Recreation Trends
DECEMBER 22, 2022
Since 2016, this award has been presented annually, and recognizes park and recreation professionals who have worked to reduce health disparities and advance systems-level change in their communities to achieve health equity. In her article, Maureen highlights winners of the RWJF-NRPA Award for Health Equity from the last seven years.

Librarian.net
FEBRUARY 10, 2024
I’ve been actively seeking out non-binary authors and trying to read print a little more. average read per month: 9.5 average read per week: 2.2 The always-updated booklist, going back to 1997, lives at jessamyn.info/booklist and it has its own RSS feed.

The Lowe Down
MAY 14, 2023
In November 2016, ownership of ONT was returned to the Inland Empire from LA County. After a period of power struggle back and forth, it was decided that ownership of ONT would be returned to the Inland Empire, with the official transfer taking place in November 2016.
Rebuilding Place in Urban Space
NOVEMBER 26, 2023
can do to start working better together as a region (Baltimore Business Journal op-ed ," 2016), and I support efforts to do this for St. Later I suggested this for Baltimore City and County (" Opinion: What Baltimore and D.C. Louis City and County (" St. Louis: what would I recommend for a comprehensive revitalization program?

Rebuilding Place in Urban Space
MAY 13, 2024
Boston versus the Raleigh-Durham's GoTransit Model ," 2017 -- " Route 7 BRT proposal communicates the reality that the DC area doesn't adequately conduct transportation planning at the metropolitan-scale ," 2016 -- " Reviving DC area bus service: and a counterpoint to the recent Washington City Paper article ," 2019 From the article: With additional (..)

Rebuilding Place in Urban Space
MAY 9, 2023
. -- " George Kelling, co-creator of the "Broken WIndows" thesis, dies " (2019) -- " The state of "broken windows" versus "problem oriented policing" strategies in 2016: Part 1, theory and practice ," 2016 -- " The state of "broken windows" versus "problem oriented policing" strategies in 2016: Part 2, what to do " -- " Night-time safety: rethinking (..)

Rebuilding Place in Urban Space
NOVEMBER 1, 2023
Strings of pink plastic balls form a ribbon along a section of Ste-Catherine Street, commonly called the Village, in Montreal, Thursday, June 23, 2016. Catherine Street in the summer, when the street is closed to traffic. THE CANADIAN PRESS/Paul Chiasson. 18 Shades of Gay The firm's website webpages on projects have great images.

Librarian.net
JANUARY 1, 2022
Previous years: 2020 , 2019 , 2018 , 2017 , 2016 , 2015 , 2014 , 2013 , 2012 , 2011 , 2010 , 2009 and some reviews from 2003. Chelsea (23) – I was the W/Th librarian for a few months. Rochester (1) – stopped by to say hello before teaching some online classes.

PMRA (Public Management Research Association)
JANUARY 19, 2017
As Vice-President and President-Elect of PMRA, I have spent the last year learning more about our thriving organization. I have been very impressed with the leadership of Don Moynihan, from whom I often receive official emails or documents at 1:00 in the morning. Don is a tireless leader who has given his all to PMRA the last few years.

Andy Feldman's Gov Innovator podcast
OCTOBER 20, 2021
Since 2016, Dr. Jenkins has been the Director of the Office of Performance and Evaluation at the Administration for Community Living (ACL) at the U.S. Since 2016, Dr. Jenkins has been the Director of the Office of Performance and Evaluation at the Administration for Community Living (ACL) at the […]

The Stoop (NYU Furman Center)
JANUARY 13, 2023
The authors find evidence that average eviction filing rates were consistently higher in public housing than in other types of subsidized housing in the pre-pandemic period (2016-2019). Cases filed due to non-payment of rent are the focus of the brief and represent the majority of eviction filings.

Rebuilding Place in Urban Space
NOVEMBER 27, 2023
I have a bunch of entries on radio: -- " Local music used to define communities: today with radio chains and national music distribution systems, not so much ," 2021 -- " Culture planning and radio: local music, local content vs. delivery nodes for a national network ," 2019 -- " Thinking anew about supporting community radio ," 2019 -- " Revisiting (..)

Rebuilding Place in Urban Space
MARCH 9, 2023
. -- " BTMFBA: the best way to ward off artist or retail displacement is to buy the building ," 2016 -- " BTMFBA: Baltimore and the Area 405 Studio ," 2021 -- " When BTMFBA isn't enough: keeping civic assets public through cy pres review ," 2016 -- " BMFBTA revisited: nonprofits and facilities planning and acquisition ," 2016 -- " BTMFBA: artists and (..)

Community and Economic Development Program of UNC
JULY 18, 2023
.” – Mayor Douglas Shere The most recent government statistics available on areas with low numbers of or access to grocery stores is from 2016, part of the federal Food Environment Atlas. By 2016, it had lost that store. In 2011, Camden County, in far eastern North Carolina, had only one grocery.

Rebuilding Place in Urban Space
NOVEMBER 20, 2023
," 2013 -- " DC and streetcars #4: from the standpoint of stoking real estate development, the line is incredibly successful and it isn't even in service yet, and now that development is extending eastward past 15th Street ," 2015 -- " The streetcar and the new potential for H Street retail revitalization ," 2016 this is an important piece.

AWS Public Sector Blog
NOVEMBER 15, 2022
After a major flood in 2016 knocked out their 911 system, they decided to use the Amazon Web Services (AWS) Cloud to become resilient against disaster, reducing service interruptions and improving response times. When a natural disaster strikes. “In

Rebuilding Place in Urban Space
JULY 13, 2023
Of course, she wrote that 60+ years ago. In a city like Washington, where the height limit constrains development, old buildings tend to get torn down and rebuilt or renovated so that they can continue to command higher rents.

Rebuilding Place in Urban Space
JUNE 27, 2024
Perceptions of public safety are shaped by cleanliness, the presence of graffiti, etc. -- " Updating the post The "soft side" of commercial district revitalization ," 2006/2016 Decades ago, DC used to pay people to clean the streets of commercial districts, but that program ended when the city was in bankruptcy. This article is interesting.

Eric Holdeman's Disaster Zone Podcast
JANUARY 31, 2023
Mr. Massey has served as the Regional Director of the DHS Cybersecurity and Infrastructure Security Agency (CISA) Region 10 office in Seattle since 2016. Mr. Massey has served as the Regional Director of the DHS Cybersecurity and Infrastructure Security Agency (CISA) Region 10 office in Seattle since 2016. Pat Massey is the guest.

Rebuilding Place in Urban Space
NOVEMBER 26, 2024
If anything it's about applying suburban ideas about bicycling (" DC as a suburban agenda dominated city ," 2013) or transit (" Transit notes #2: Anti-transit opposition a form of defending automobility as a way of life ," 2016) to urban areas.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content